“Nothing is impossible”

Teaching staff, students, doctoral candidates and young scientists demonstrated the research strengths of computer science at Darmstadt University of Applied Sciences at the faculty’s first Research_Day@FBI. Eight ongoing projects were presented. Researchers reported on their experiences and the results of their work at information booths and in lectures.
By Astrid Ludwig, 20.7.2023
Christoph Busch still clearly remembers one of his first days as a newly appointed professor at Darmstadt University of Applied Sciences back in 2005. Research, a colleague told him at the time, was not possible at a university of applied sciences. This was something that Busch, an enthusiastic computer scientist and former Head of Department for Security Technology for Graphics and Communication Systems at the Fraunhofer Institute for Computer Graphics Research (IGD) in Darmstadt, could neither imagine nor accept. Today, 18 years later, Professor Busch is one of the university’s most acclaimed researchers and much in demand as an international biometrics expert. He has since published almost 700 papers and reaped a number of awards, including 2nd place in the 2022 German IT Security Award of the Horst Görtz Foundation. “Nothing is impossible,” he said. Words of encouragement for the audience attending his lecture, which opened the Research_Day@FBI.
Practical advice
This was the first time that the Faculty of Computer Science had held its own Research Day. “We want to show how we conduct research in our faculty,” explained Martin Stiemerling, Professor of Data and Telecommunications Networks, head of the da/net research group and the driving force behind the event. The faculty wants to raise its visibility among an external audience as well as within the university and to present “what we are doing and which research projects are currently topical.” The target group for the Research Day included partners from industry and business, but also the students themselves, as the faculty wants to inspire them for research. That is why Martin Stiemerling, as the event organiser, chose a format for the first Research Day that offered room for discussion, exchange of ideas and presentation of projects. What is important is “research that you can live and breathe,” says Professor Busch, which is why “we intentionally chose experienced and successful colleagues for the lectures who can give practical advice.”
Among them was Professor Thomas Döring from the university’s Service Centre for Research and Transfer (SFT), who reported on how h_da supports researchers. The centre assists, for example, in the acquisition of research projects, as well as offering help and advice in the search for suitable cooperation partners and funding programmes. The staff also help researchers to prepare applications as well as with project management and commercialisation of project results.
Enthusiasm and tolerance
Biometrics professor Christoph Busch gave the guests a kind of “recipe” for good research: “All cooks use water. The secret is the ingredients and the spices.” He advised students and researchers to look for a topic that is particularly relevant, to avoid competition within the university if possible, and to form teams instead. It is important, he said, to listen very carefully to what users need and where the deficits lie. In his experience, dedication and enthusiasm, as well as tolerance “when faced with harsh feedback” are necessary. And Busch had another piece of advice: “Just be bold.”
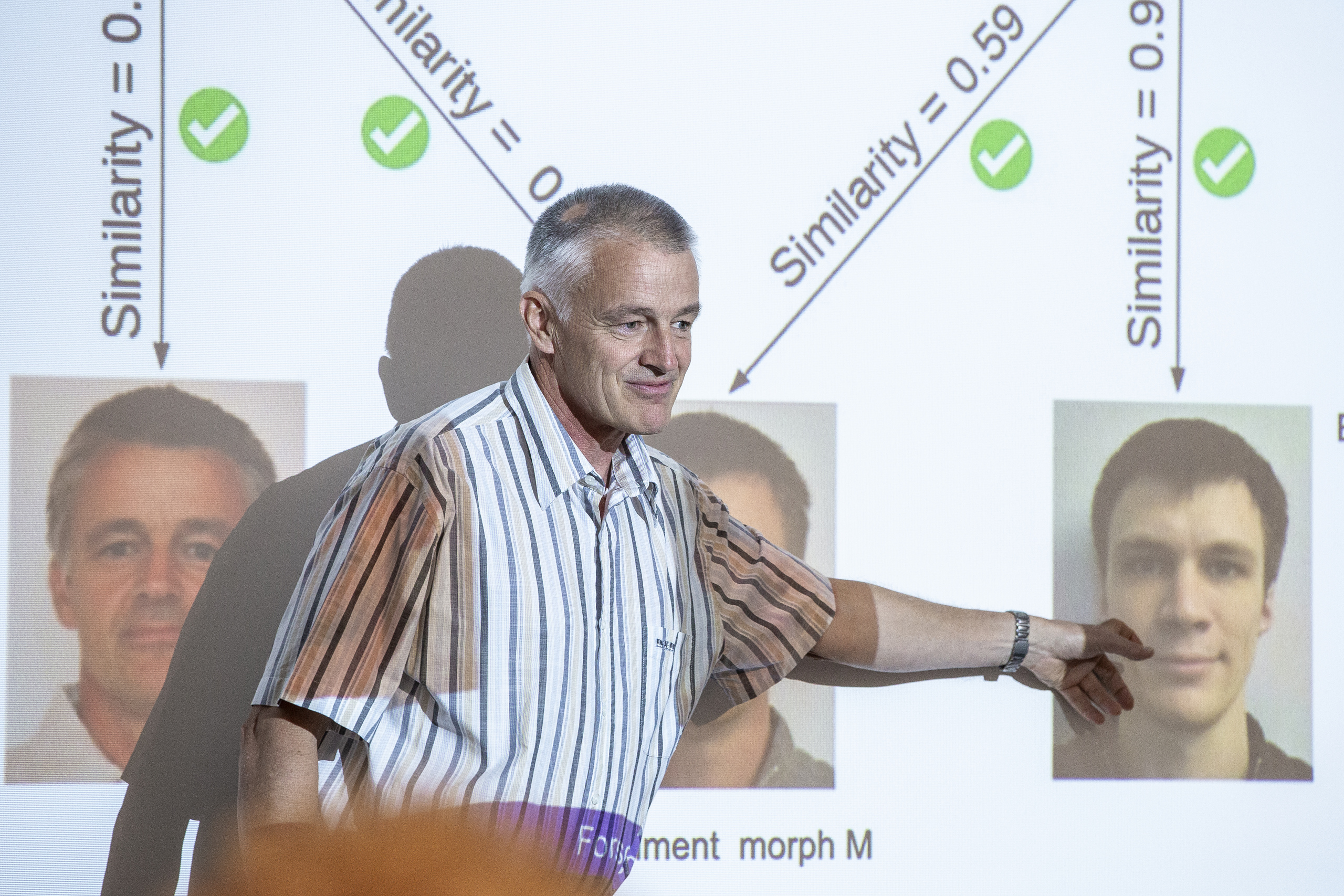
Expert for morphing attacks
Professor Busch is meanwhile an internationally acknowledged expert in biometrics and cybersecurity. He works, for example, with Germany’s Federal Office for Information Security (BSI) and holds a second professorship in Norway. In addition, h_da shares his biometrics course with a university in Denmark. One of his areas of specialisation is the detection of morphing attacks. A morphing attack is, for example, when fraudsters use passports with morphed photos for illegal entry and border crossing. Morphing is the process of making one biometric photo out of two on a computer. In this way and because of the great facial similarity, two people can use the same passport. Professor Busch and his research group have developed a system for morphing attack detection and also delivered recommendations on how to combat it, which were incorporated into Germany’s new Passport Act in 2020. Busch was very pleased to be part of the first Research Day and full of praise: “It’s nice that there is now such a day at the faculty,” he said. There are plans to repeat the event.
How to deal properly with cyberattacks
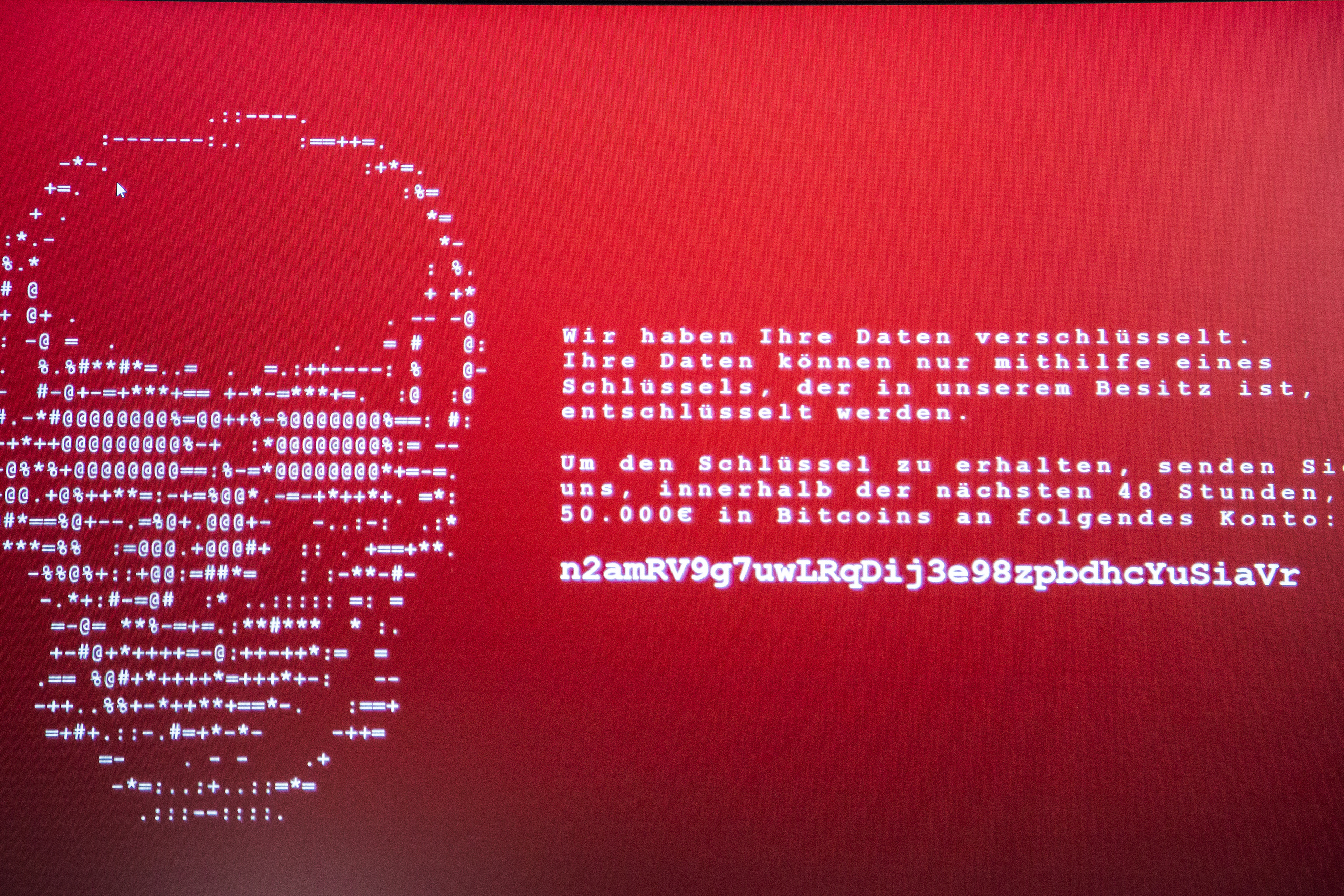
Security and protection against cyberattacks were the subject of several research projects at once. Patrick Renkel, a research associate at the faculty, has been working and conducting research within the “User-Centred Security” working group since 2021. In the ELITE project, the working group focuses on users and is looking primarily at private individuals as well as small and medium-sized enterprises. “We want to draw their attention to the dangers and introduce the topic of cybersecurity into companies on a larger scale,” says Renkel. Extortion attempts by cybercriminals who steal or encrypt data are on the increase. Employees need to learn how to recognise such online attacks more easily and how to deal with them. “Most of them only know that you shouldn’t open unfamiliar email attachments, for example.”
However, the young researchers also want to show in their project what is behind such cyberattacks and how the attackers proceed. They have developed a platform that simulates phishing and ransomware attacks as realistically as possible. In a secure training environment, they present various scenarios to the participants, and suitable learning material and courses show them how to deal with cyberattacks properly as well as “what you can do if you are affected,” explains Renkel. Germany’s Federal Ministry for Economic Affairs and Climate Action is funding the project within the “Cybersecurity for SMEs Initiative”. Here, Darmstadt University of Applied Sciences is collaborating with the University of Hamburg, the Fraunhofer Institute for Industrial Engineering (IAO) and the Fraunhofer Institute for Open Communication Systems (FOKUS). The ELITE demonstrator was already presented at the Hannover Messe and is to be made freely available as open source software in the autumn.
Spot the jammer
“We’re an alarm system.” This is how Professor Stefan Valentin describes his latest research results on “Jammer detection in 5G campus networks with machine learning”. “Jammer” is the term for special transmitters of jamming signals that can be used to attack mobile networks such as 5G campus networks. Nationwide, over 500 licences have been issued for campus networks, which are particularly suitable for mission-critical applications such as industrial automation. The Networking Technologies research group has developed a solution that recognises when these networks are exposed to what are known as “denial-of-service attacks” at the physical level. “Jammers can disrupt the entire network and make communication physically impossible,” says Professor Valentin. Such a jamming attack is often used to cover up data theft. “Our research project uses state-of-the-art AI methods to detect both simple as well as smart jammers in real time, in order to locate them and to react automatically,” he explains. The project’s official title is ADWISOR5G. It is being implemented in cooperation with industrial users and has been funded by Germany’s Federal Office for Information Security with around €1.8m since June 2023.
Tap-proof exchange of encryption keys
End-to-end encryption – most of us are familiar with this principle from cell phone messengers or online banking. But when the quantum computer arrives, such – currently state-of-the-art –encryption methods will in future be useless within seconds. That is why da/net, a research group at h_da, is occupying itself with the exchange of quantum-safe keys in networks in its project “Quantum Key Exchange in the German Telecommunications Network for Greater IT Security” (DemoQuanDT). The group is looking at how to implement secure key exchange via several quantum transmission links, explains Professor Martin Stiemerling. So far, these quantum links have a range of 80 to 150 kilometres, but the DemoQuanDT researchers are working on a link of up to a thousand kilometres composed of several individual links. In the first instance, this research is important for large companies and banks that communicate with each other. The collaborative project (https://danet.fbi.h-da.de) has been awarded funding of €1m by Germany’s Federal Ministry of Education and Research.
Post-quantum cryptography
It is no longer a question of if but only of when the quantum computer will arrive. Current cryptography, the encryption of data, will then no longer offer any protection. That is why the Applied Cyber Security Darmstadt (ACSD) research group is tackling this threat to cybersecurity from various perspectives. The project “Post-Quantum Password Authenticated Key Encapsulation for eCards” is dealing with how the authentication procedure for electronic ID cards and passports can be made more secure. Until now, this procedure has been based on cryptosecurity protocols that a future quantum computer could quickly crack, says Nouri Alnahawi, a doctoral candidate and research associate at h_da. To overcome this, the research team is developing quantum-safe protocols for electronic ID cards. Within this collaborative project, h_da is working together with TU Darmstadt and ATHENE, the National Research Centre for Applied Cybersecurity. Another project, called PORTUNUS, is about helping programmers to select cryptographic algorithms, as Professor Alexander Wiesmaier explains. “Not every computer scientist is also a cryptographer,” says Wiesmaier, which is why the researchers are developing a tool that helps them to automatically select the “right” algorithms on the basis of context information.
Safe vehicles
For demonstration purposes, there was an e-car right outside the door, and interested visitors could take a look under the bonnet. Full of high-tech and IT systems, technological advances and increasing connectivity in modern vehicles offer not only comfort but also new loopholes for attackers. “In the worst case scenario, they can have a life-threatening effect,” says Professor Christoph Krauß. As part of the Automotive Security research unit, the ACSD research group is studying these loopholes and developing new cybersecurity and privacy solutions.
At the Research Day, Professor Krauß and doctoral candidate Timm Lauser demonstrated how two possible attacks on a Volkswagen ID.3 might look. In the first scenario, the attacker has gained control of a steering device in the vehicle’s electrical system and can access the vehicle’s automotive Ethernet via it to manipulate the rearview camera by removing an obstacle in the video stream, for example. In the second scenario, the attacker can access the infotainment system via WLAN. This would allow them to set the volume irreversibly to the maximum. Both could potentially cause an accident. The h_da researchers are rooting out these vulnerabilities and showing “what you can learn from these attacks and how you can protect yourself against them,” says Christoph Krauß.
Visual hearing aid
Udo Gebelein, a lecturer at h_da, and Stefan Rapp, Professor of Computer Engineering, Embedded Graphics and Foundations of Computer Science at the university, have designed a very practical aid for people with hearing impairments. To localise from which direction sounds are coming, they have constructed a sound tracking system equipped with a display, a single-board computer and microphones. The computer visualises the sounds as blue lines on the screen. The prototype is now running on a smartwatch, and the researchers want to integrate the tiny computer into the frame of a pair of spectacles. Initial tests with people with hearing impairments have been positive, reports Professor Rapp. The researchers are currently looking for medical technology partners. “It’s a small project without much financial support,” says Rapp.
Digital, resilient cities
How can we make the digital infrastructure of cities more resilient to crises? How, for example, can we continue to maintain mobility as well as the electricity and water supply during storms, climate disasters or cyberattacks? These are questions that Professor Eva Brucherseifer is dealing with in a joint research project between h_da and the German Aerospace Centre (DLR). In her present work, for example, she is building an IT platform with “digital twins”. The purpose of these duplicates of important infrastructure facilities is to deliver information on what to do in the event of a crisis. They are training objects and “at the same time we can learn how to improve our infrastructure and make it more resilient,” says Professor Brucherseifer. Moreover, such a platform should provide easily comprehensible information for crisis units. “It needs to be clearly understandable so that employees know how to respond.” The project will run for three years, and the aim is also to bring experts from other engineering disciplines on board, for example. “We’re still at an early stage,” says Eva Brucherseifer.
Contact
Christina Janssen
Science Editor
University Communication
Tel.: +49.6151.533-60112
Email: christina.janssen@h-da.da
Translation: Sharon Oranski