HECA

With their digital technology, electronic control units and interfaces, the cars of today are highly integrated rolling computers. This makes the emergency vehicles of the police or fire brigade interesting targets for cyber attacks. The HECA research project, “Hardening emergency vehicles to protect against cyber attacks”, aims to counter this. On behalf of the Hessian Ministry of the Interior, for Security, and Homeland Security, computer science professors Christoph Krauß and Stefan Valentin and their team are putting police vehicles to the acid test.
By Daniel Timme, 4.9.2025
999. The control room receives the emergency call on a hot and humid afternoon: a bank robbery! “All available forces to the western industrial estate immediately!” Policewoman A rushes to her vehicle, presses the remote key – nothing. The doors won’t open. The crew of patrol car B is already on the way and radios headquarters: “Are the robbers armed?” The reply from the vehicle’s loudspeakers: a pop song blaring at full volume. Vehicle C races towards the destination entered in the satnav – but false coordinates make it miss the exit.
“Everything is going to plan, guys. You’ve got a head start,” tells Mr X his accomplices. He is watching the operation from his desk. Via monitors, he can track live the GPS positions of the police vehicles involved and what their front cameras are recording. A bank robbery made easy. What sounds like a second-rate crime drama on TV is, unfortunately, not so far-fetched at all.
Script kiddies and dangerous felons
How can ambulances or the emergency vehicles of police forces and fire brigades be protected against cyber attacks? This is the initial question and task of the HECA project headed by automotive expert Professor Christoph Krauß, who is supported by his colleague Professor Stefan Valentin, a computer scientist and radio expert. Doctoral students Hannah Nöttgen and Matteo Varotto are working on subareas of the project. A Bachelor’s student and a student assistant complete the team.
“Opportunities to attack arise wherever communication is involved,” says Krauß. Asked about attackers and their motives, he says: “The spectrum is broad. It starts with what we call ‘script kiddies’ – people who, without being particularly IT-savvy, use off-the-shelf programmes to test what havoc they can wreak.” Some individuals might find making life difficult for the emergency services amusing. The fun stops when it puts people in danger, especially when the attackers can be ascribed to organised crime and the purpose of the attack – as in the fictional example – is to prepare the ground for foul play.
Krauß formulates his project team’s central questions as follows: “What threats are there? How could attackers access police vehicles, monitor them, disrupt or deactivate their technical systems?” The IT security experts call these “attack vectors”: ways and means that unauthorised individuals use to gain access to computer networks, systems or applications by exploiting security flaws. This is how attackers obtain information or manipulate systems.
The Hessian Ministry of the Interior, for Security, and Homeland Security (HMdI) is funding the project with around €338,000 from October 2024 to September 2026. Project partner is the Hessian police, specifically the Hessian State Criminal Police Office and the police’s Technology Division. “The ministry is familiar with the requirements, and it coordinates and networks all the relevant stakeholders,” says Krauß, praising the collaboration. “We have regular online calls with the police.” In addition, there are meetings in Wiesbaden and Darmstadt when vehicles are brought in or exchanged. “The police can directly influence which aspects we prioritise. We align our research with the requirements.”
Christoph Krauß – the automotive expert
Christoph Krauß has been Professor for Network Security at the Faculty of Computer Science since 2015 and heads the research group Applied Cyber Security Darmstadt (ACSD) together with Professor Alexander Wiesmaier. Krauß’s research interests include automotive security and privacy, railway security, IoT security, and post-quantum cryptography. Krauß is co-founder and Head of Automotive Security Research at INCYDE GmbH. He is spokesperson for the IT Security Expert Group, a member of the Faculty Council, the inter-university Doctoral Centre Applied Informatics (PZAI) and the management board of the Research Centre Applied Informatics (fz ai).
From GPS and Wi-Fi to OBD2, USB, and DAB
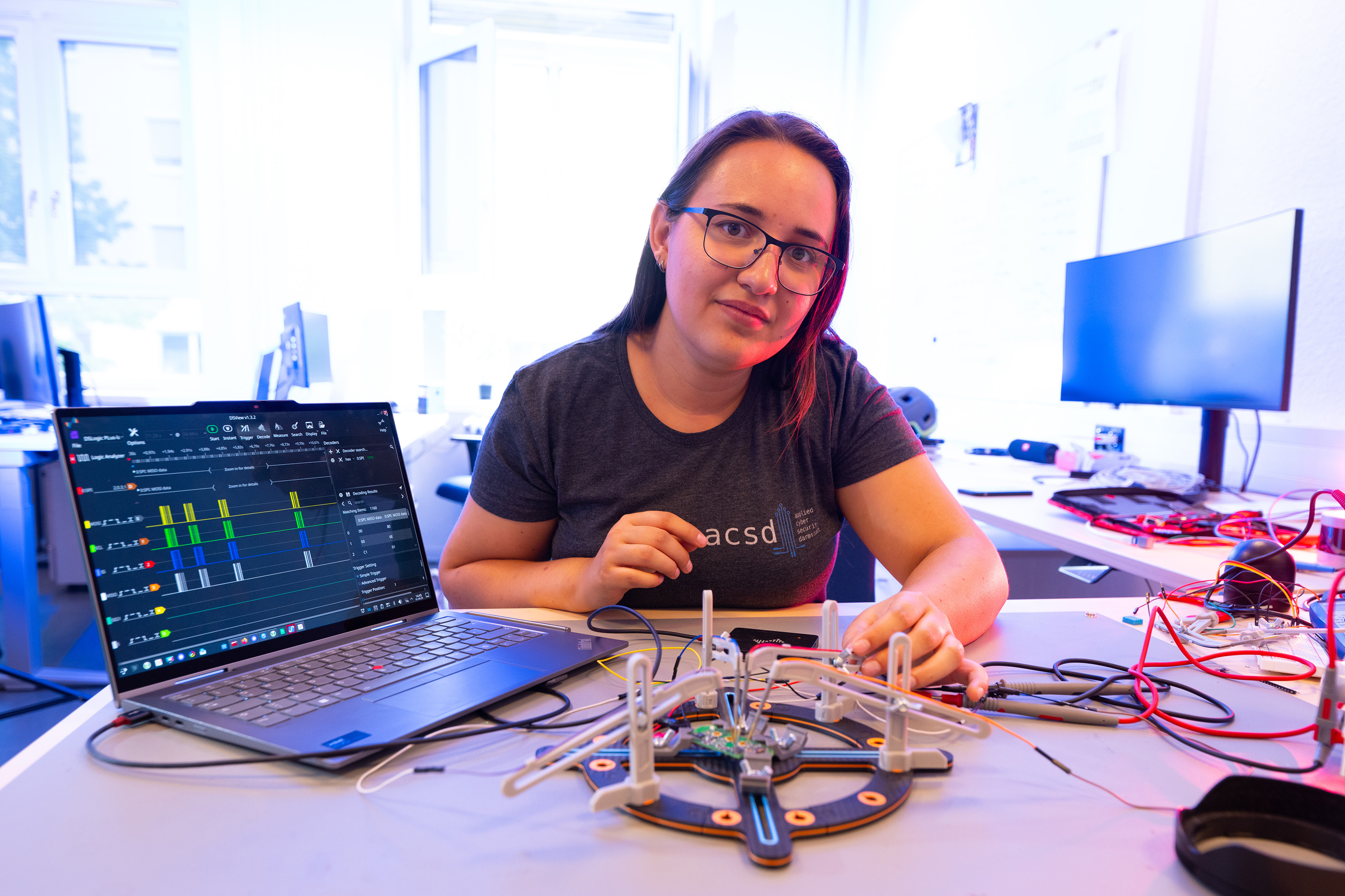
“Physical access to the vehicle is often the first step to further attacks,” says Hannah Nöttgen, describing her area of responsibility. “I’m the wireless guy,” says Matteo Varotto, introducing himself with a wink. He is focusing on radio signals. Both observe a lack of awareness of data protection in relation to cars. “Many people are meanwhile watchful of data security on their smartphones. But only few think about what information their cars give away about them,” says Matteo. “Modern cars are data leeches,” warns Hannah.
Vehicles have long been equipped with mobile communication systems, GPS, Wi-Fi, Bluetooth, and USB ports on board. The team is looking closely at these communication channels and interfaces, which are attack vectors. There are also points of attack that are typical for specific vehicles. First, there is the OBD2 interface, the on-board diagnostics system in common use since the early 2000s. Via the socket, which is usually installed in the driver’s footwell, it is possible to read out not only the functions of emissions-related systems and electronic control units. “Many manufacturers meanwhile also use it to update firmware,” says Christoph Krauß.
As wireless communication between modern cars and other vehicles, road users or smart infrastructure increases, known in technical terms as “Vehicle-to-Everything” (V2X), this also creates attack vectors. HECA, however, also has potential attack points on its radar that are less conspicuous. Krauß says: “DAB radios have also already been manipulated.” So much for pop songs.
Differentiating and classifying data streams
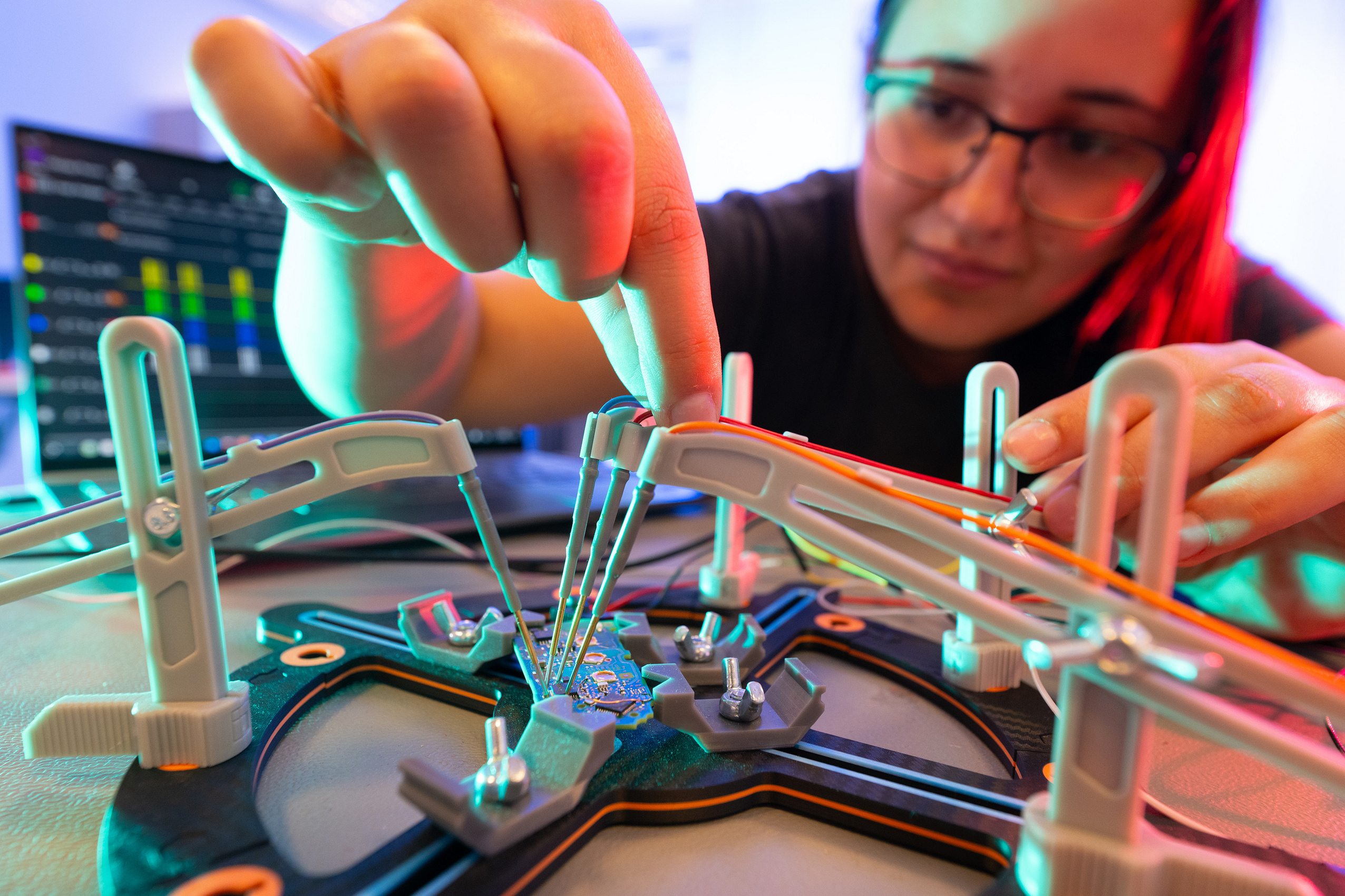
“To get a feel for where to start and to find viable approaches, at the beginning of the project we experimented in a more playful way,” says Krauß. They then selected suitable methods. In an iterative process, two phases constantly alternate: “First, we identify attack vectors and simulate attacks – then we develop ways to harden the vehicles.” In computer technology, the word “hardening” in the project title means upgrading a system’s security. “Differentiating and classifying data streams is a very important aspect for us,” says Krauß. By way of example: When the car is in operation, the driver needs the navigation system. For this, the vehicle downloads maps and traffic data. At the same time, however, it should not reveal its location to potential attackers. The project team has been given a clear mandate: interventions must be non-invasive – i.e., no cutting cables or snapping antennas – and flexible in terms of time, i.e. it must be possible to activate them temporarily.
“We look at attack vectors in detail and at various levels – physics, communication, and cryptography,” explains Stefan Valentin. “In HECA, we systematically investigate what data the vehicles transmit and what data they receive.” Here, software-defined radios (SDRs) play an important role. “These are programmable transmitters and receivers,” says Valentin. “The computer processes wireless signals in software, and transmits or receives them with minimal radio-specific hardware.” This makes it easy to test, demonstrate and implement prototypes that previously called for the building of chips. SDRs can receive, record, and analyse radio signals, but also play them back, i.e., reproduce recorded signals or generate manipulated signals.
Stefan Valentin – the radio expert
Stefan Valentin has been Professor for Mobile Networks at the Faculty of Computer Science as well as a member of the Faculty Council and the Doctoral Centre Applied Informatics (PZAI) since 2018. Together with the Faculty of Electrical Engineering and Information Technology, he heads the 5GLab and is a senior member of the Networking Technologies Research Group. Valentin is founder of the Steinbeis Transfer Centre Wireless Technologies as well as co-founder and CTO of the startup Open Radio Systems GmbH. In his research, he explores methods for 6G mobile communications and for the physical layer security of wireless networks. His algorithms are deployed in mobile networks around the world and over 30 patent applications have been filed for them. Among other work, he has developed jammers and jamming countermeasures for Germany’s Federal Office for Information Security (BSI).
Attack on distance estimation
Application example: With the keyless locking systems today, it is possible to open a car door and start a vehicle without having to insert a key into a lock or press a button on the key. Attackers exploit this for what are called “relay attacks”: they position transmitters and receivers between the vehicle and the key, intercept the radio signal, redirect it and can then unlock the vehicle. Distance estimation developed by vehicle manufacturers on the basis of ultra-wideband radio signals is intended to prevent this. “A challenging task in the project is an attack on this distance estimation that bypasses this security feature,” says Valentin.
Inside and in front of Building D21, the team puts a second-hand VW Passat, a new Mercedes-Benz Vito, and an electric VW ID.3 to the acid test. “We work with current models, but we are also keeping an eye on future technical challenges,” says Christoph Krauß. One example is the charging connectors on electric vehicles, via which information is also exchanged with the charging infrastructure.
Something else that the HECA team is testing is the targeted disruption of wireless communication by means of jamming. A jammer transmits signals that disable communication. The jammers developed have a short range so that they only interfere with the vehicle and not, for example, with emergency calls in the vicinity. Valentin gives a typical example of an application: “It can protect against spying by preventing the transmission of the vehicle’s location data.”
Technological coherence gives greater leverage
Most of the team’s findings are transferable to other emergency vehicles. This is at least as important because if a fire engine were to be directed to the wrong place or an ambulance to be disabled, this could quickly cost lives. Many of the project results might even have more fundamental benefits, says Krauß: “The technical basis of police vehicles is the same as that of normal cars, so most of what we are developing is also relevant for standard vehicles.” This means that HECA could also make vehicles safer that are not equipped with blue lights and radios.
In the first half of the project, the HECA team worked on stationary or slow-moving vehicles. They will soon be shifting into higher gears. “We plan next to conduct attacks at high speeds in a secure environment,” says Krauß. They have already asked if they can use a police training ground. The HECA team at h_da is doing everything they can to make it more difficult for attackers to hack vehicle systems and for Mister X and his buddies to be met with “Access denied”.
Contact the h_da scientific editorial team
Christina Janssen
Science editor
University Communications
Tel.: +49.6151.533-60112
Mail: christina.janssen@h-da.de
Translation: Sharon Oranski
Photography: Markus Schmidt
Never mind the Polizei – here’s the FB I
Faculty of Computer Science: bi.h-da.de/
Interested in studying computer science?
fbi.h-da.de/en/study-with-us/interested-students/study-information
Related articles on impact
Car Hacking (2021)
Interview RESURREC (2023)
Project NERO I (2023)
Vehicle-to-Game (2024)
Project NERO II (2025)